Why Are Strings Immutable in Java? Best Practices and Use Situations
Why Are Strings Immutable in Java? Best Practices and Use Situations
Blog Article
The Advancement of Immutable String Handling: An Essential Element of Software Application Development
In the detailed realm of software development, the handling of unalterable strings stands as a foundation that has undergone significant advancement in time. From its humble beginnings to the complicated challenges run into in early executions, the journey of immutable string control has been a critical aspect of software application design. As we navigate through the historical landscape of this basic idea, tracing the advancements, security effects, and emerging trends, we find ourselves at a point where the inherent worth of understanding this advancement becomes increasingly noticeable.
Beginnings of Unalterable Strings
The concept of immutable strings traces back to the early days of programs languages when developers sought to enhance the dependability and safety of information handling mechanisms. Immutable strings describe strings that can not be changed after they are created. This basic idea was presented to resolve issues regarding data stability and protect against unplanned alterations to vital info saved as strings.

Moreover, unalterable strings add to enhancing the overall protection of software program systems (Why are strings immutable in Java?). By stopping unapproved parties from tampering with sensitive string information, immutable strings aid mitigate the danger of data breaches and unapproved access to secret information. This fundamental principle remains to play a critical duty in modern-day shows languages and stays a foundation of robust and secure software advancement practices
Very Early Obstacles and Solutions
One of the primary obstacles in handling unalterable strings was taking care of memory efficiently. In addition, guaranteeing that strings continued to be unchanged shown to be complex, especially when numerous components of the codebase needed to gain access to and modify data.
To address these challenges, designers started implementing information encryption methods to secure sensitive info saved in immutable strings. By incorporating security and hashing approaches into the handling of unalterable strings, programmers substantially improved the protection and integrity of information within software systems.
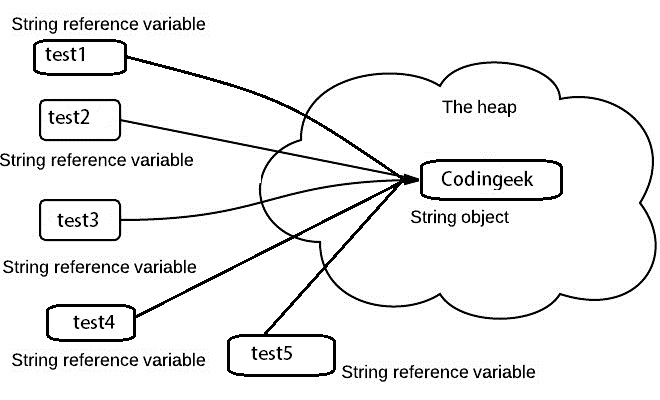
Advancements in String Immutability
In software program development, a noteworthy advancement in the handling of unalterable strings has actually arised through developments in data file encryption and hashing techniques. By employing safe hash algorithms like SHA-256 or cryptographic methods such as AES file encryption, programmers can make sure that sensitive details saved in immutable strings remains protected and tamper-proof. These improvements have actually bolstered the integrity and privacy of data within applications, particularly in industries where information security is vital, such as money, health care, and cybersecurity.
Additionally, innovations in string immutability have actually led the method for enhanced efficiency optimization. Unalterable strings enable a lot more effective memory management and caching approaches, lowering the overhead related to frequent string manipulations (Why are strings immutable in Java?). This optimization not just boosts the total responsiveness of software program applications yet additionally contributes to better scalability and resource use
Safety Effects and Finest Practices
With the foundation laid by improvements in string immutability, recognizing the protection implications and applying finest techniques ends up being extremely important in protecting delicate data within software applications. Unalterable strings play an important function in enhancing protection by protecting against unapproved adjustments to data, making sure data stability throughout the application's lifecycle. By utilizing unalterable strings, designers can mitigate usual vulnerabilities such as injection strikes, buffer overflows, and information tampering, which are usually manipulated by harmful actors to compromise systems.
To improve security further, ideal techniques must be followed when dealing with delicate information. This consists of encrypting information at remainder and en route, implementing appropriate gain access to controls, employing safe coding methods, and regularly upgrading software application elements to spot well-known vulnerabilities. Furthermore, developers ought to comply with the concept of the very least privilege, ensuring that only required approvals are provided to users and procedures. By incorporating these safety steps and best techniques into software application development procedures, organizations can better protect their data properties and decrease the risk of safety and security breaches and information leakages.
Future Trends in String Handling
Amidst the ever-evolving landscape of software program development, the trajectory of string handling is poised to witness significant advancements and technologies. Among the key future patterns in string handling is the raising focus on performance optimization. As software applications continue to grow in complexity and range, the reliable handling of strings ends up being important for preserving optimal efficiency. Programmers are discovering new formulas and data frameworks to improve the rate and effectiveness of string operations.
Additionally, an additional pattern coming up is the assimilation of expert system (AI) and useful reference artificial intelligence (ML) in string pop over here taking care of tasks. AI-powered devices are being established to automate and simplify numerous string adjustment processes, leading to enhanced performance and accuracy in software program advancement process.
Moreover, there is an expanding focus on enhancing the safety and security elements of string managing through progressed security techniques and safe coding practices. As cyber hazards continue to evolve, making sure the integrity and privacy of data within strings is coming to be a top concern for programmers. By embracing robust security procedures, such as file encryption at rest and in transit, designers can alleviate the risks related to string control vulnerabilities.
Verdict
To conclude, the development of unalterable string handling has actually been an essential element of software development, beginning with its beginnings to the advancements made in the last few years. Early difficulties have actually been attended to through cutting-edge options, resulting in improved security methods in taking care of strings. It is necessary for designers to stay upgraded on the most up to date trends in string immutability to make certain the toughness and security of their software application applications.
Immutable strings refer to strings that can not be changed after they are created. Why are strings immutable in site here Java?. By preventing unapproved parties from meddling with delicate string data, unalterable strings help alleviate the danger of data breaches and unapproved access to confidential details. By including security and hashing methods into the handling of immutable strings, designers dramatically improved the safety and reliability of data within software application systems
Immutable strings allow for more efficient memory monitoring and caching approaches, minimizing the overhead linked with frequent string adjustments. Unalterable strings play a critical duty in boosting safety and security by preventing unapproved modifications to information, guaranteeing data honesty throughout the application's lifecycle.
Report this page